1. Active Password Changer


With this tool, you can change the passaword that is in the computer that you can physically access. This tool works pretty well. There are some features it possesses, namely booting from USB drives, floppy disks, or via CD. In fact, this tool also provides a simple CD burner to burn the files on a CD.
2. Cain


This is one tool that is very popular among the hacker. This application is known as a versatile application, not just that used to do kracking password, other features can also be found here, such as MITM. This application allows the agan-agan to obtain the hash values from various sources.
3.dumpacl-dumpsec


Tools used to perform the job enumeration. First, the application is called Dump ACLs. How it works utilize Connections Null, so this tool is capable of displaying user accounts in detail.Examples such as when the last change or change a password, administrator whom and when expirednya etc.
4.Handy-keylogger

Just like other keylogger, it can also hide itself if detected from the Task Manager. This keylogger secretly records all activity on your PC agan an installed application. Such as keyboard typing, clipboard, snapshots, and addresses of all websites visited can be recorded by either using this application.

Just like other keylogger, it can also hide itself if detected from the Task Manager. This keylogger secretly records all activity on your PC agan an installed application. Such as keyboard typing, clipboard, snapshots, and addresses of all websites visited can be recorded by either using this application.
5. L0phtkrack Administrator


With this application, agan can mengimmpor hash value from another computer by using one of the features it has that is imported hashes. But agan skalian still must have a user account with administrator equivalent. If agan want to take a hash value remotely.
6. privacy keyboard


Applications ni useful tool to prevent keylogger that hurt agan skalian system. Whether it is a keylogger that works in hardware or software. If the application is active you can not do a screen capture of shoots, keystroke. To keylogger type of hardware, this application provides a virtual keyboard, so it will not be detected.
7. Spytech Spy Agent


Application of this spy will record all the information carried by the user in secret. Logyang file used to store the recording will be encrypted. By default, the hotkey for this application menjalaknnya is Ctrl + Shift + Alt + M, but it still defalt hotkey you may modify in accordance with the wishes of all Agan-agan
8.winfingerprint-0.6.2


This application menggambungkan many enumeration technique. In this application you can see through the Net BIOS enumeration, SMB, MSRPC, SNMP, and Active Directory. You can just enter the IP address of the host you want to check and select the scan button to start scanning.After that, it's up-agan agan want diapain tuhkomputr remote.
9. Sams Big Play Maker
Application of this one is unique because it can hide hidden text or message that you enter becomes like a form of conversation. Ordinary they will not realize that there was a hidden message in it.
Application of this one is unique because it can hide hidden text or message that you enter becomes like a form of conversation. Ordinary they will not realize that there was a hidden message in it.
10. Tracks eraser Pro
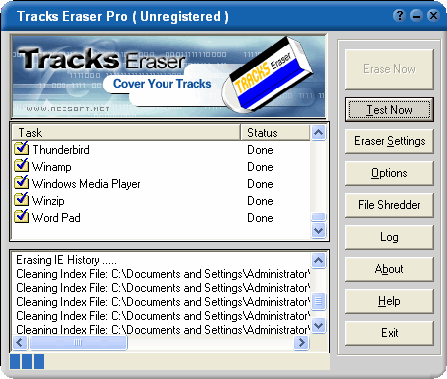
In matters erase the traces, this application is very reliable, because it supports many types of applications. In addition to the log removes recorded by Windows, this application will remove traces of Office applications, RealOne player, media player, winzip, winamp, and so forth. Guaranteed gan-agan will not leave traces in other PCs.

In matters erase the traces, this application is very reliable, because it supports many types of applications. In addition to the log removes recorded by Windows, this application will remove traces of Office applications, RealOne player, media player, winzip, winamp, and so forth. Guaranteed gan-agan will not leave traces in other PCs.
11. Actual Spy